Secure your cluster and receive runtime security alerts on Slack.
Falcosidekick
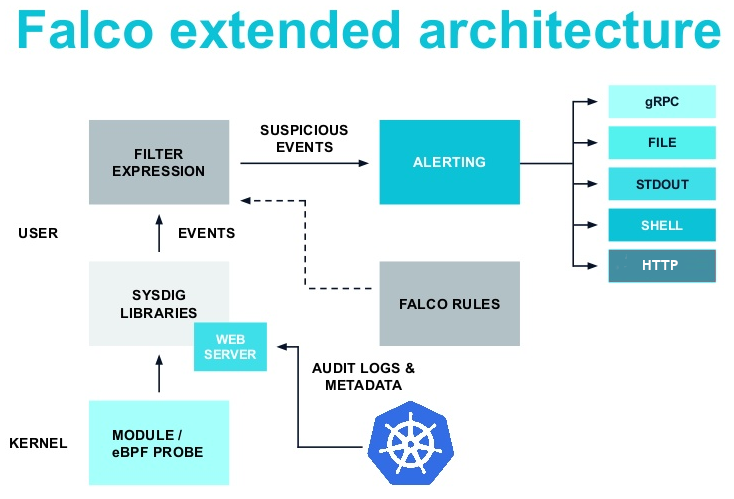
Why Falcosidekick?
Falco has five outputs for the events: stdout, file, gRPC, shell and http. Even if they’re convenient, you can quickly be limited to integrating Falco with other components. Here comes Falcosidekick, a little daemon that extends that number of possible outputs.
The available Falcosidekick outputs are namely, Slack, Mattermost, Teams, Datadog, and others. Falcosidekick also provides metrics about the number of events and lets you add custom fields in events, for example environment, region, and others.
How to integrate Falcosidekick with a Kubernetes cluster?
Before you begin
- Install Helm 3
- Create a K3s cluster and ensure that you are able to access it. For more information about how to create a K3s cluster, see deploying a K3s cluster.
- Install Kubectl
- Ensure that you are able to access the cluster from outside the cluster. To manage K3s from outside the cluster, copy the contents of
/etc/rancher/k3s/k3s.yamlfrom your K3s to~/.kube/configon an external machine where you have installed kubectl, replacing127.0.0.1with the IP address of your Server. - Create a Slack Webhook. Note: Keep it secret, keep it safe. Your webhook URL contains a secret. Don’t share it online, including via public version control repositories. Slack actively searches out and revokes leaked secrets.
-
Create a falco namespace:
kubectl create ns falco -
Update your helm repo:
helm repo add falcosecurity https://falcosecurity.github.io/charts helm repo update -
Install Flaco and Falcosidekick
helm install falco falcosecurity/falco --set falcosidekick.config.slack.webhookurl=https://hooks.slack.com/services/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 --set falcosidekick.config.debug=true --set falcosidekick.enabled=true --namespace falcoAn output similar to the following appears:
WARNING: Kubernetes configuration file is world-readable. This is insecure. Location: /Users/rkodhandapani/.kube/config NAME: falco LAST DEPLOYED: Mon Feb 1 08:52:43 2021 NAMESPACE: falco STATUS: deployed REVISION: 1 NOTES: Falco agents are spinning up on each node in your cluster. After a few seconds, they are going to start monitoring your containers looking for security issues. No further action should be required. rkodhandapani@rkodhandapani-C02XG0X6JG5H ~ % kubectl get -n falco pods NAME READY STATUS RESTARTS AGE falco-b92nr 1/1 Running 0 55s falco-6m4j8 1/1 Running 0 55s falco-falcosidekick-767547c756-srzz8 1/1 Running 0 55s ```
Explore Falcosidekick Web User Interface
-
Install Falco and Falcosidekick:
helm install falco falcosecurity/falco --set falcosidekick.config.slack.webhookurl="https://hooks.slack.com/services/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" --set falcosidekick.image.tag=ui --set falcosidekick.enabled=true --namespace falco
An output similar to the following appears:
```
WARNING: Kubernetes configuration file is world-readable. This is insecure. Location: /Users/rkodhandapani/.kube/config
NAME: falco
LAST DEPLOYED: Mon Feb 1 08:52:43 2021
NAMESPACE: falco
STATUS: deployed
REVISION: 1
NOTES:
Falco agents are spinning up on each node in your cluster. After a few
seconds, they are going to start monitoring your containers looking for
security issues.
No further action should be required.
rkodhandapani@rkodhandapani-C02XG0X6JG5H ~ % kubectl get -n falco pods
NAME READY STATUS RESTARTS AGE
falco-b92nr 1/1 Running 0 55s
falco-6m4j8 1/1 Running 0 55s
falco-falcosidekick-767547c756-srzz8 1/1 Running 0 55s ```